Talk to an Expert
How to Detect and Prevent Social Engineering Attacks
Have you encountered social engineering during your business journey? Chances are, you have. If you’ve ever received phishing emails or cyber threats, you’ve been the target of a social engineering scheme.
Unfortunately, this threat is here to stay. And as technology improves, so do social engineering techniques. You need to know what you’re up against so you can protect your employees and your business. We’ll cover everything from identifying threats to preventing attacks in this guide.
What is social engineering?
Social engineering is a form of manipulation that involves coercing people into performing specific actions or giving up confidential information. These manipulation tactics exploit people’s emotions and willingness to help in urgent matters. Fraudsters and customers alike can engage in social engineering for different reasons.
Typically, fraudsters use social engineering to get access to sensitive information. For example, a fraudster may pretend to be a co-worker with an urgent problem requiring access to company login credentials, financial information, or personnel files. The employee, feeling a sense of obligation to help, may give the information to the fraudster without question.
There are also cases of customers using social engineering tactics to get refunds for items they don’t want to return. Essentially, they get goods for free by manipulating customer service agents. Some customers may even go as far as hiring a refunding service to get refunds for them.
Common Types of Social Engineering Attacks
Social engineering encompasses a variety of attack methods. We’ll cover the most common types that we see businesses dealing with today.
Phishing attacks
Phishing happens when a fraudster sends a message or email to a victim posing as a trusted authority figure. The message may include a link to a fake website or a link that will install malware on the user’s device, giving the fraudster access to all stored login information.
Employees at any company are susceptible to these attacks and should be discouraged from clicking on a link from a suspicious email or text.
Note: There is a subset of phishing called spear phishing, where a fraudster targets a specific individual or organization.
Pharming
Pharming involves luring a user onto a fake website designed to look like a legitimate site to steal login credentials or personal information. For example, fraudsters may create a website that looks identical to a national bank’s site and redirect web traffic from the real site to the fake one. Then when users log in, the website collects their data and hands it over to the fraudster.
Pretexting
Pretexting is a method of manipulating victims by making up a situation that requires the victim’s cooperation. For example, fraudsters often use pretexting in elder fraud scams. They pose as the victim’s grandchild and claim to be in some kind of trouble. So they need the grandparent to send money to get out of the situation.
Scareware
Scareware is a tactic that involves tricking a victim into thinking their computer is infected with malware. Often, it appears in the form of a pop-up message claiming the computer is infected with a virus and offers a software solution. However, when the target downloads the solution, they inadvertently install malware on the computer.
Baiting
Baiting occurs when a fraudster leaves a malware-infected device, like a USB flash drive, in a place where someone is sure to find it. When the target plugs it into their computer, they unintentionally install the malware. Companies that work with sensitive data are easy targets for this kind of attack.
SIM swap
A SIM swap attack happens when a fraudster gains control over a victim’s mobile phone number so that they can receive text and calls. Typically, the fraudster pretends to be the victim and calls the mobile phone company’s customer service staff to get the SIM swapped.
Deepfake schemes
Deepfake technology uses artificial intelligence and machine learning to create synthetic or manipulated digital content like images, video, audio, and text for fraud. Fraudsters use this technology to impersonate business executives and gain access to company assets and financial accounts.
How to Detect Social Engineering Threats
Most social engineering attacks follow a pattern — often called the attack cycle.
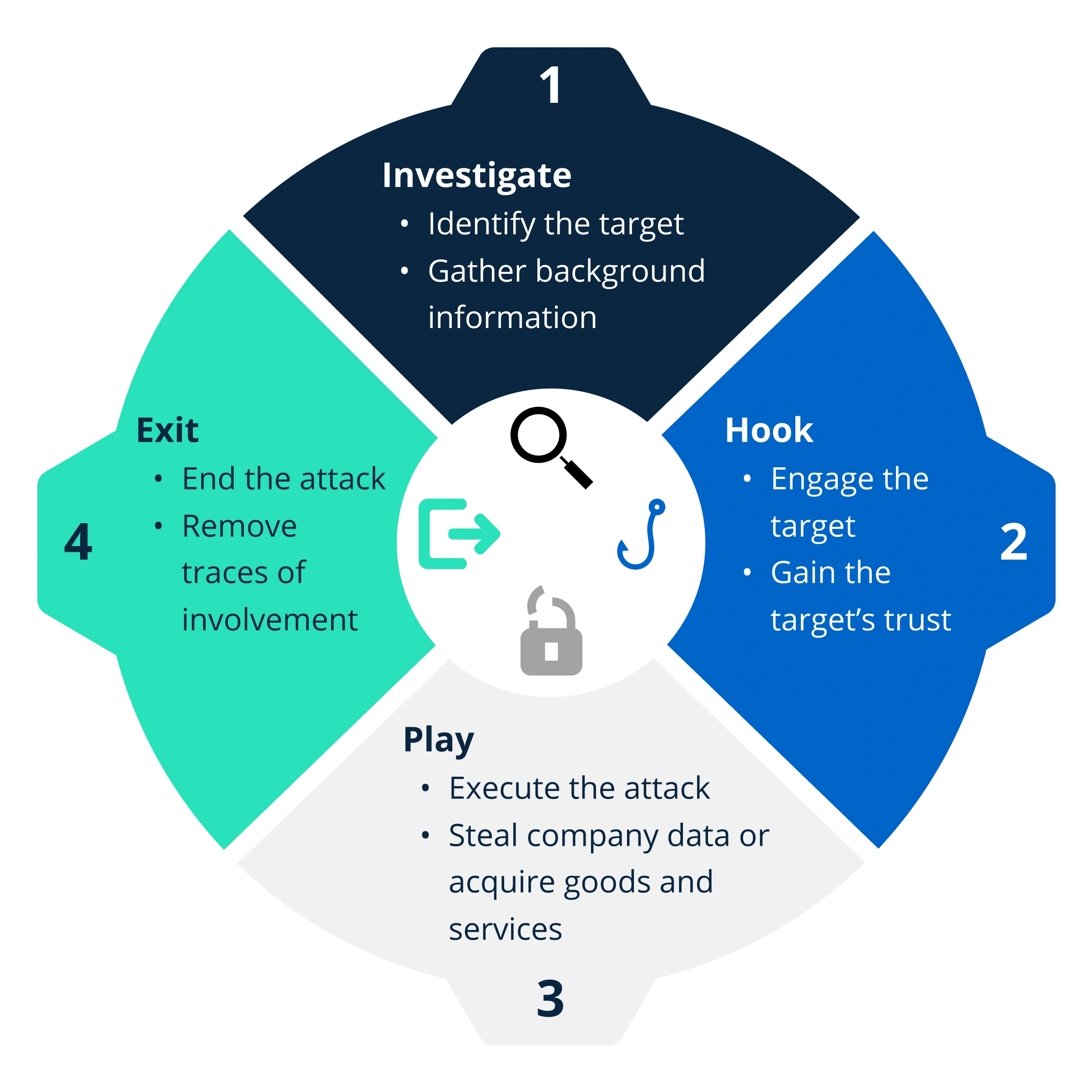
Most tactics prey on human vulnerabilities and emotions. You can spot the pattern if you know what the common warning signs of an attack are.
Urgent requests to take action.
When a fraudster sends a suspicious email or text that includes an urgent request for personal information, it’s almost always a sign of social engineering at play. Any kind of communication that demands a user to take action immediately — especially if it’s coming from an unknown sender — should be investigated.
Offers that are too good to be true.
Offers that sound too good to be true often are. A fraudster may send an offer for free access to an app, game, or program in exchange for login credentials. But many free apps or software can contain malicious code, especially through unsolicited online offers. Sometimes the offers could be as simple as information about a lucrative job opportunity.
Unexpected links or attachments.
Many social engineering schemes send victims links to fake websites or downloads of malware via email or text. Usually, these links are sent unprompted by the victim. You can often tell these messages are scams because the text may be misspelled or the grammar might be slightly off.
Suspicious email addresses or phone numbers.
Most scams are conducted through email, phone calls, or text messages. Often, the fraudster pretends to be from a reputable source, such as a bank or utility company. However, the communication usually comes from an email address or phone number that doesn’t match the company’s public contact information. For example, the email address might look like a legit business email but one or two characters might be off.
Threats or intimidation.
Threats are a common tactic used by fraudsters and sometimes customers to manipulate others. For example, customer service agents are often evaluated according to the number of positive reviews they receive and may be disciplined for poor reviews. Customers and refund service providers may use that fact to their advantage and threaten to leave a bad review or complain to the agent’s manager to get a refund.
7 Tips for Preventing Social Engineering
Though no single method is fool-proof, there are several ways to protect your business from social engineering attacks.
1. Require security awareness training.
One of the best countermeasures against social engineering is education. Employees often need to be reminded about the role they play in keeping data and company accounts safe. Require regular security training to reduce the likelihood that one of your employees might inadvertently give away sensitive information.
Research shows that training can significantly reduce the risk of a security threat. In fact, one study cited that 80% of organizations surveyed say security awareness training has reduced phishing susceptibility.
2. Establish and test an incident response plan.
Along with training, a good way to prevent threats is by developing an incident response plan and testing your employees regularly. This incident response plan should walk your employees through the appropriate steps to take when an event — such as a spam email or suspicious request — happens.
Once you have a plan in place, test your employees on a regular basis. Send test phishing emails to all the employees in your organization and track how they respond to the threat. Monitor whether or not they follow the incident response plan.
3. Invest in anti-malware software.
Despite your efforts to train and test your employees, things still happen. Employees accidentally click on harmful links or wind up on malware-infected sites. You need to have back up security just in case these accidents happen. Invest in a good anti-malware software and put it on all company devices.
4. Block and filter access to sites on company devices.
In addition to protective software, consider installing content blockers and spam filters on company devices. That way, you can prevent employees from going to certain sites altogether — like social networking apps that waste time, sites that are infected with malware, and external file-sharing sites.
5. Implement a robust verification process.
Protect your company accounts by requiring a thorough verification process for logins. Passwords are one way of protecting accounts, but in today’s world, they simply aren’t enough. Implement an additional protocol like multi-factor authentication, which typically requires users to submit a code sent via email or text and a password in order to log in.
We know this step may sound like it’s adding too much friction or frustration for your employees. But think of it this way. When employees log in to company devices, they have access to incredibly sensitive information — like intellectual property, personnel files, and more. It’s worth the extra security measures to protect that data.
6. Train customer service agents to recognize red flags.
Unfortunately, a lot of social engineering schemes target customer service staff — especially those that work in returns departments. The best thing you can do is arm them with the resources they need to identify and respond to signs of social engineering attacks.
Educate your staff on common real-life scenarios often by sending monthly emails updating them on new threats and scams. Also provide a detailed response procedure so that your customer service agents can confidently respond to aggressive or manipulative customers.
7. Consult fraud experts.
Another way to combat social engineering is by seeking help from an expert. Fraud prevention providers, like Kount, often offer additional consulting services for risk management. These experts deal with social engineering events daily across all industries, so they can recommend policies that are right for your business.